This question, everyone will ask is, what are your tricks to pass the CCNA 200-301 exam? That must be using the latest 200-301 dumps. Which dumps to choose is a challenge. For this reason, I recommend two plans for you to refer to, so you can compare.
For the latest dumps of CCNA 200–301, you can try Pass4itSure 200–301 dumps: https://www.pass4itsure.com/200-301.html and Actual4test. They are popular sites for purchasing exam dumps.
| 1. actual4test.com | $59.99 | Q&A: 875 Questions and Answers |
| 2. pass4itsure.com | $45.99 | Q&As: 1205 Questions and Answers |
A simple comparison I believe you should have a conclusion!
The Pass4itSure 200-301 dumps won easily
Pass4itSure provides you with personalized services with a simple and convenient purchase page, the most authentic 200-301 dumps learning materials, and presented in PDF and VCE formats, with diversified choices.
- PDF Only: $45.99
- Software Only: $49.99
- Software + PDF: $59.99
(Three prices, three options, of which the PDF+VCE combination is more cost-effective)
And Pass4itSure beat Actual4test with an absolute price advantage and a total number of questions!
For a better understanding, we provide you with the latest free 200-301 Q&A:
Question 1:
Which QoS queuing method discards or marks packets that exceed the desired bit rate of traffic flow?
A. shaping
B. policing
C. CBWFQ
D. LLQ
Correct Answer: B
Question 2:
Which field within the access request packet is encrypted by RADIUS?
A. authorized services
B. authenticator
C. username
D. password
Correct Answer: D
Question 3:
Drag and Drop
Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right.
Select and Place:
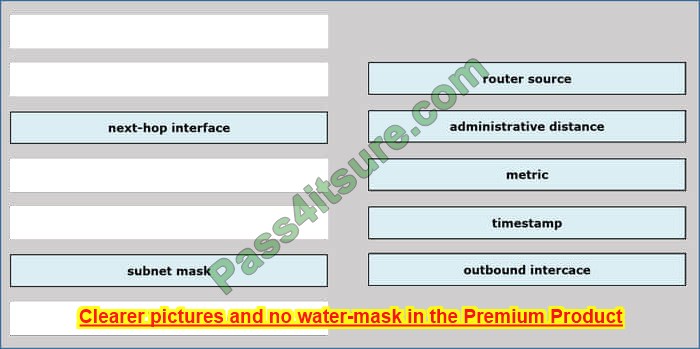
Correct Answer:
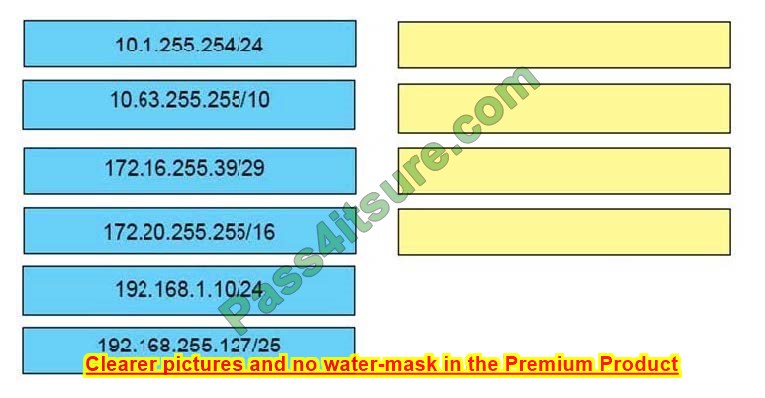
This subnet question requires us to grasp how to subnet very well. To quickly find out the subnet range, we have to find out the increment and the network address of each subnet. Let\’s take an example with the subnet 172.28.228.144/18:
From the /18 (= 1100 0000 in the 3rd octet), we find out the increment is 64. Therefore the network address of this subnet must be the greatest multiple of the increment but not greater than the value in the 3rd octet (228).
We can find out the 3rd octet of the network address is 192 (because 192 = 64 * 3 and 192 < 228) -> The network address is 172.28.192.0.
So the first usable host should be 172.28.192.1 and it matches with the 5th answer on the right. In this case, we don’t need to calculate the broadcast address because we found the correct answer.
Let \’s taking another example with subnet 172.28.228.144/23 -> The increment is 2 (as /23 = 1111 1110 in 3rd octet) -> The 3rd octet of the network address is 228 (because 228 is the multiply of 2 and equal to the 3rd octet) -> The network address is 172.28.228.0 ->
The first usable host is 172.28.228.1. It is not necessary but if we want to find out the broadcast address of this subnet, we can find out the next network address, which is 172.28. (228 + the increment number).0 or
172.28.230.0 then reduce 1 bit -> 172.28.229.255 is the broadcast address of our subnet. Therefore the last usable host is 172.28.229.254.
Question 4:
Which network allows devices to communicate without the need to access the Internet?
A. 172.9.0.0/16
B. 172.28.0.0/16
C. 192.0.0.0/8
D. 209.165.201.0/24
Correct Answer: B
This question asks about the private ranges of IPv4 addresses. The private ranges of each class of IPv4 are listed below:
1. Class A private IP address ranges from 10.0.0.0 to 10.255.255.255
2. Class B private IP address ranges from 172.16.0.0 to 172.31.255.255
3. Class C private IP address ranges from 192.168.0.0 to 192.168.255.255
Only network 172.28.0.0/16 belongs to the private IP address (of class B).
Question 5:
How does authentication differ from authorization?
A. Authentication is used to verify a person\’s identity, and authorization is used to create syslog messages for logins.
B. Authentication is used to determine what resources a user is allowed to access, and authorization is used to track what equipment is allowed access to the network.
C. Authentication verifies the identity of a person accessing a network, and authorization determines what resource a user can access.
D. Authentication is used to record what resource a user accesses, and authorization is used to determine what resources a user can access.
Correct Answer: C
Question 6:
Which three statements are typical characteristics of VLAN arrangements? (Choose three.)
A. A new switch has no VLANs configured.
B. Connectivity between VLANs requires a Layer 3 device.
C. VLANs typically decrease the number of collision domains.
D. Each VLAN uses a separate address space.
E. A switch maintains a separate bridging table for each VLAN.
F. VLANs cannot span multiple switches.
Correct Answer: BDE
Question 7:
Which two statements are true about the command ip route 172.16.3.0 255.255.255.0 192.168.2.4? (Choose two.)
A. It establishes a static route to the 172.16.3.0 network.
B. It establishes a static route to the 192.168.2.0 network.
C. It configures the router to send any traffic for an unknown destination to the 172.16.3.0 network.
D. It configures the router to send any traffic for an unknown destination out the interface with the address 192.168.2.4.
E. It uses the default administrative distance.
F. It is a route that would be used last if other routes to the same destination exist.
Correct Answer: AE
Question 8:
Refer to the exhibit.

Which command provides this output?
A. show ip route B. show cdp neighbor
C. show ip interface
D. show interface
Correct Answer: B
Question 9:
Which configuration management mechanism uses TCP port 22 by default when communicating with managed nodes?
A. Ansible
B. Python
C. Puppet
D. Chef
Correct Answer: A
Question 10:
Which of the following is the JSON encoding of a dictionary or hash?
A. {“key”: “value”}
B. [“key”, “value”]
C. {“key”, “value”}
D. (“key”: “value”)
Correct Answer: A
Question 11:
Which implementation provides the strongest encryption combination for the wireless environment?
A. WPA2 + AES
B. WPA + AES
C. WEP
D. WPA + TKIP
Correct Answer: A
Question 12:
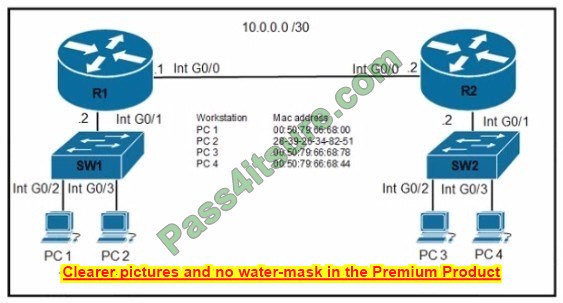
Refer to the exhibit.
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
ipv6 unicast-routing statement included (IPv6 is enabled on the router). Compared to the exhibit, Fa0/0 and Fa0/1 have correct configurations. The route to subnet 2001:db8:4::/64 points to R18\’s Fa1/0 (correct next-hop).
Question 13:
DRAG DROP
Drag the descriptions of IP protocol transmissions from the left onto the IP traffic types on the right.
Select and Place:

Correct Answer:
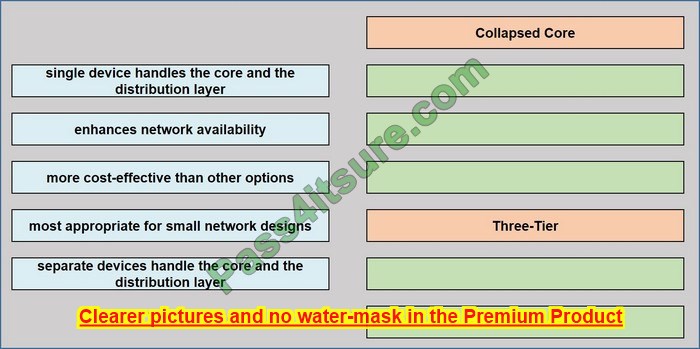
Question 14:
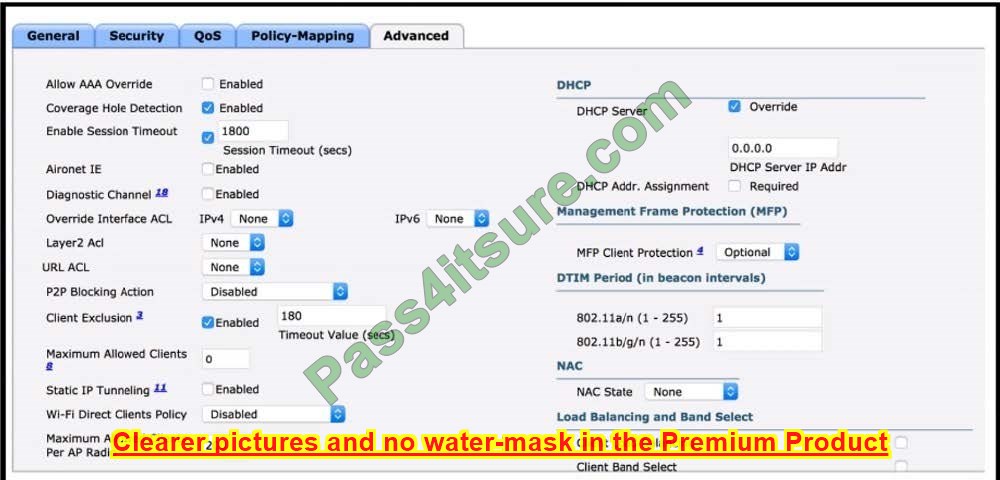
Refer to the exhibit. What must be configured to enable 802.11w on the WLAN?
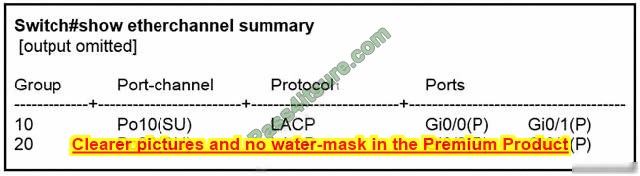
A. Set PMF to Required.
B. Enable MAC Filtering.
C. Enable WPA Policy.
D. Set Fast Transition to Enabled
Correct Answer: A
Question 15:
Refer to the exhibit. When PC-A sends traffic to PC-B, which network component is in charge of receiving the packet from PC-A verifying the IP addresses, and forwarding the packet to PC-B?
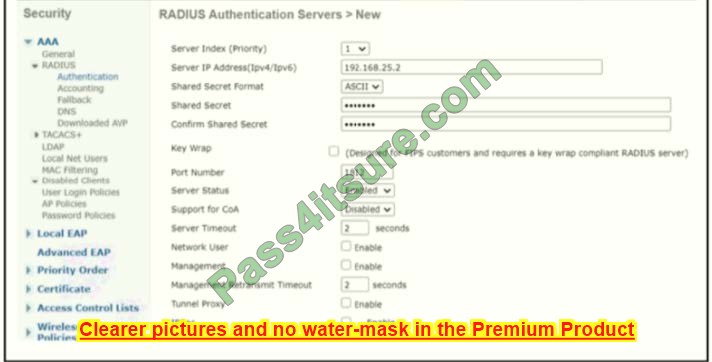
A. Layer 2 switch
B. Router
C. Load balancer
D. firewall
Correct Answer: B
PC–A and PC-B are not in the same network. Switches send traffic in layer 2 and within the same VLA while routers route traffic to different subnets and at layer 3.
Our experts also provide free 200-301 PDF files, to help you pass the exam: https://drive.google.com/file/d/1_cRoAyec2CHnwI5mExIJHV6REAbNOEyR/view?usp=share_link
All of the above free exam questions and answers are from the Pass4itSure 200-301 dumps https://www.pass4itsure.com/200-301.html (Q&As: 1205), ensuring the latest updates.
All study guide: Free Cisco (Cisco Certified) dumps list:
Summary:
The CCNA 200-301 exam is not difficult, and the choice is important. Be sure to make sure the 200-301 dumps are up-to-date and reliable. The comparison found that the Pass4itSure 200-301 dumps are your best choice, and then arrange your time reasonably, practice the test carefully, and Cisco CCNA certification is yours.
Good luck with a high score on the exam.